Cisco Catalyst: Understanding Cloud Monitoring vs. Cloud Management
Cisco has been making significant changes to its Digital Network Architecture (DNA) offerings, particularly with the rebranding of DNA Center to...
Did you know that IOS updates are available from Cisco and DO NOT always require a SMARTnet contract?
If access to IOS updates is important to you, I suggest you take a read. The primary reason that SMARTnet is purchased on a large portion of hardware is simply due to the fear of not having an update if one were needed.
So, let's first specify that there are two different categories of hardware. The first is critical core-level type hardware. This can include core switching, routers, and firewalls. The second category is pretty much everything in the access layer and then those items that do not actually have standalone IOS, like APs or fabric extenders. ‘Everything in the access layer’ is typically more than 60% of your physical inventory of hardware.
I’m going to present two strategies for your to obtain IOS updates without requiring a SMARTnet contract. The first is utilizing Cisco’s Software Update Policy for Catalyst and the second is utilizing Cisco’s Product Security and Incident Response Team (PSIRT).
Before I go any further, I want to clarify that ‘IOS Updates’ and ‘IOS Upgrades’ are different. You can read more about that at Cisco IOS Updates vs Upgrades
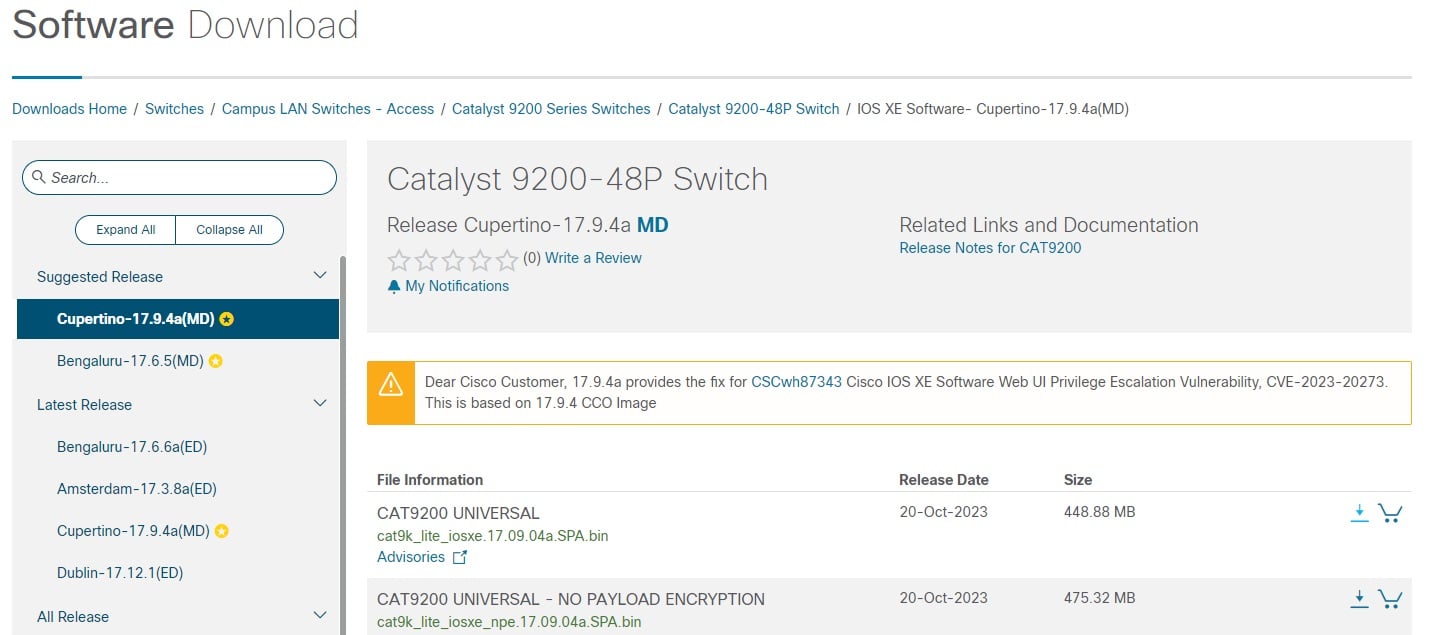
Hopefully, this isn’t news to you but Cisco has offered IOS updates without requiring SMARTnet for their Catalyst access switches since 2009. It's pretty easy to prove that TAC and hardware replacement costs don’t even come close to justifying the recurring cost of SMARTnet, especially for your lower-end (technically) access switches.
The only Catalyst switch that does not offer IOS updates without SMARTnet is the Catalyst 6500. Every other model including Catalyst 2000, 3000, 4000, 9200, 9300, 9400, 9500, and 9600 switches DO NOT require SMARTnet in order to get updates. The other caveat is the policy is only for LAN Base and IP Base. Advanced feature set images are not included. I’ve copied the links below as well as listed the models below. All you need is a Cisco CCO login to access all of the different versions of the code.
Cisco Catalyst 2000 Series:
◦ Cisco Catalyst 2960, 2960-S, 2960-X, 2960-XR, 2960-L, and 2960-Plus Series Switches
◦ Cisco Catalyst 2960-C and 2960-CX Series Compact Switches
Cisco Catalyst 3000 Series:
◦ Cisco Catalyst 3850 and 3650 Series Switches
◦ Cisco Catalyst 3750-X and 3560-X Series Switches
◦ Cisco Catalyst 3750-E and 3560-E Series Switches
◦ Cisco Catalyst 3750V2 and 3560V2 Switches
◦ Cisco Catalyst 3750 and 3560 Series Switches
◦ Cisco Catalyst 3560-C and 3560-CX Series Compact Switches
Catalyst 4000 Series:
◦ Cisco Catalyst 4500E Series Switches
◦ Cisco Catalyst 4500 Series Switches
◦ Cisco Catalyst 4500-X Series Switches
Catalyst 9000 Series:
◦ Cisco Catalyst 9200 and 9200L Series Switches
◦ Cisco Catalyst 9300, 9300L, and 9300X Series Switches
◦ Cisco Catalyst 9400 and 9400X Series modular access switches
◦ Cisco Catalyst 9500 and 9500X Series fixed core and aggregation switches
◦ Cisco Catalyst 9600 and 9600X Series modular core switches
The second way to get an updated IOS image without having a SMARTnet contract is by leveraging Cisco’s Product Security and Incident Response Team, also known as PSIRT.
**Please note that the Level 1 engineers who initially answer TAC MAY NOT know about PSIRT. Follow the instructions below and ask to be escalated if you’re having issues. You can also call us for help.
https://sec.cloudapps.cisco.com/security/center/resources/security_vulnerability_policy.html#ire
So what is the PSIRT?
Firstly, it's based on ISO/IEC 29147:2018 https://www.iso.org/standard/72311.html which is from the International Organization for Standardization and requires all OEMs to be responsible for notifying and fixing software with known security vulnerabilities. Or in other words, someone above the OEMs wants to ensure that the data traversing network hardware is secure whether that particular network manager purchases SMARTnet or not.
From Cisco’s Security Vulnerability Policy:
Cisco Product Security Incident Response
The Cisco Product Security Incident Response Team (PSIRT) is responsible for responding to Cisco product security incidents. The Cisco PSIRT is a dedicated, global team that manages the receipt, investigation, and public reporting of information about security vulnerabilities and issues related to Cisco products and networks. Cisco defines a security vulnerability as a weakness in the computational logic (e.g., code) found in software and hardware components that, when exploited, results in a negative impact on confidentiality, integrity, or availability.
So, code updates to fix known security vulnerabilities are available for any Cisco device (not just Catalyst access hardware). There is one catch in that you need to specify which specific code you can move to compared to having a SMARTnet contract where you can download any image that you want. The image that you can obtain is simply a ‘fixed’ image that specifically addresses the security vulnerability that you are calling about. You’ll notice that multiple software images are offered to fix various vulnerabilities. You’ll also notice that nearly every ‘fixed’ image will also have known security vulnerabilities, so you kind of work your way through the process and ultimately end up with one of the most current images that are published.
The process to identify security vulnerabilities and then obtain the fixed images can be a little lengthy, but likely well worth the investment compared to the cost of SMARTnet.
If you have questions about PSIRT, please contact your Edgeium representative.
Cisco has been making significant changes to its Digital Network Architecture (DNA) offerings, particularly with the rebranding of DNA Center to...
Cisco has rolled out yet another layer to their support services—Success Tracks. If you're already familiar with SMARTnet, you might be wondering...

A new security vulnerability pushed Cisco to urge enterprise administrators to install critical security updates. As always, a SMARTnet contract is...